
Three-Word Password Attacks
The idea behind three word passwords as a concept is in my opinion a nice nudge in the right direction, In a perfect world, a passphase or a sentence
The idea behind three-word passwords as a concept is, in my opinion, a nice nudge in the right direction, In a perfect world, a passphase or a sentence ... well, actually in a perfect world, two memorable passphrases, one to get you into your computer, and the other your password manager, the password manager relinquishing you of the need to remember any password, and thus, allowing you to go mental when cranking up the password/passphrase complexity
I wrote a script that combines words in the Oxford 5000 in combinations of 3 until it's exhausted, and that's the wordlist

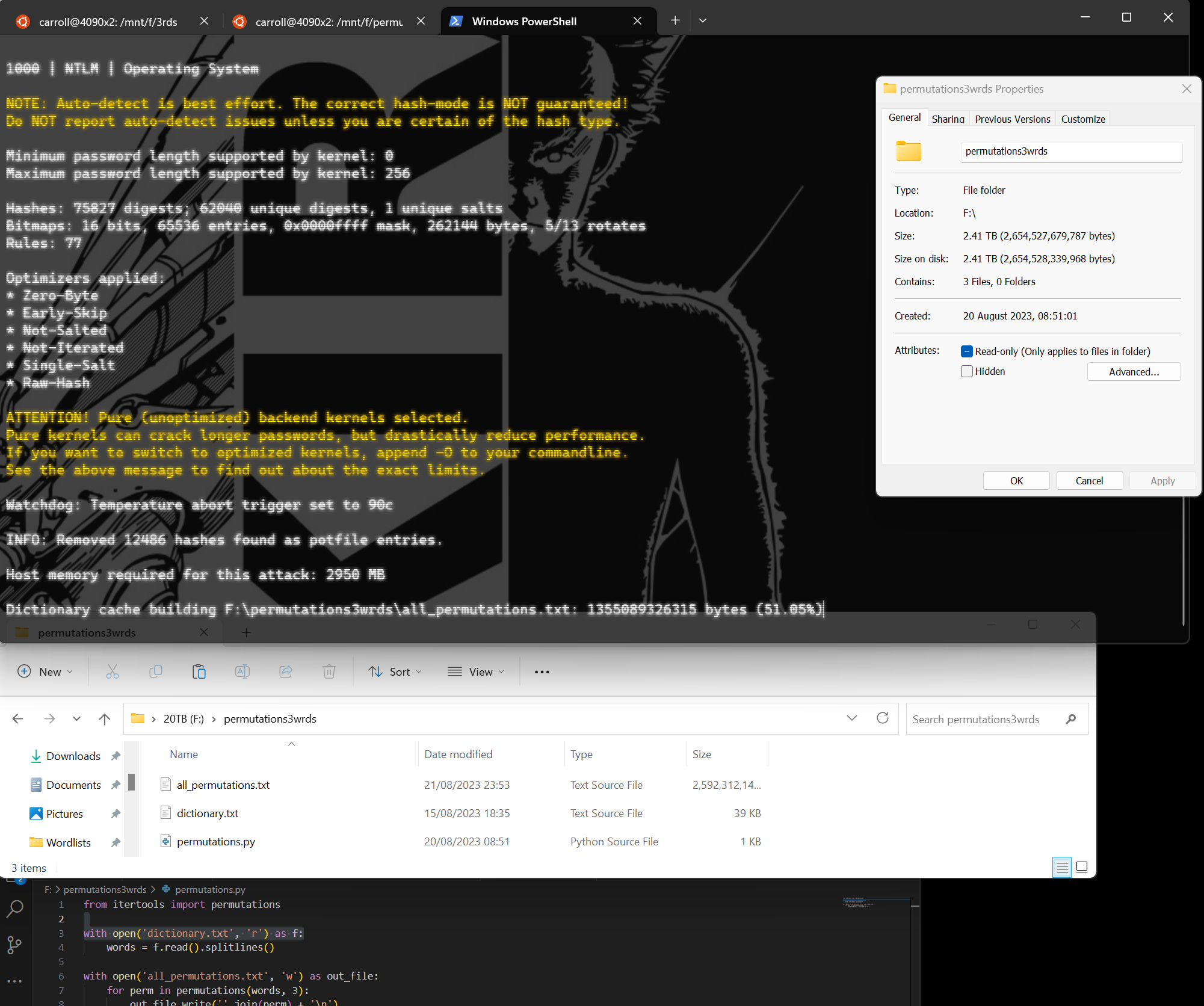
We are left with a 411 Gb 2.4 TB text file that contains three of the words in all combinations per line, if we were to do every English word available ... well, the math ... if we were being generous with how many words there are in the English language and we where to repeat the combinations we'd be looking at (finger in the air) 166.7 quadrillion combinations, about 3 yottabytes of storage (WTF is that?!) and about 66 years on a modern high-end CPU assuming your code is optimised.
So, this is probably the leanest best means to reach these three-word style passwords
The first step is to get the Oxford5000, this is actually the Oxford 3000 + the top up to make it 5000, and even then it's not actually 5k ... anyway.
We need the raw text, I found them here:
https://github.com/jnoodle/English-Vocabulary-Word-List/tree/master
Add the 5000 into the 3000, the 5000 is actually close to two thousand, but the expectation is you already have the three, so you merge them together for the full 5k
Following along, the dictionary above and the following python is all you need to recreate the beasty 3 word list, a whopping () before introducing rules, hashcat is telling me it will take just short of 8 hours to run the 2.4tb list + best64.rule
from itertools import permutations
with open('dictionary.txt', 'r') as f:
words = f.read().splitlines()
with open('all_permutations.txt', 'w') as out_file:
for perm in permutations(words, 3):
out_file.write(''.join(perm) + '\n')
Initially, I wanted to capitalise on all cores of my computer but that makes this problem more of a problem than I care for, I'm happy running this on one core for 20 hours, but if someone wants to make a version that uses more cores and produces no duplicates, in much less time I'd love to see it, altho I have the outcome I wanted, it's a bit of an unscratched itch.
You have your 5000 words saved to dictionary.txt, you have Python installed, you have a big storage medium, and you're good to go.
I might update this page with a torrent of the file, but i'm not sure if it's just easier to produce your own, go on, roll your sleeves up.
Having a three-word password is probably better than what you're normally doing, if you're on your journey to enhance your 'password' perhaps moving to three words is the right move incrementally, unless you're using sentences or passphrases as passwords, or hang in there for passwordless authentication ... but we seemed to have normalised this idea that staff are too ... thick? to do this, yet they're trusted to perform the requirements of their post and protect the data they are in the custody of ... I think that needs a rethink.
A Shout out to Aiden who spent a fair slice of the weekend exploring what looks like a simple challenge: https://aidanmitchell.uk/posts/an-exercise-in-profiling-python/