
Installation Security Considerations
A little tip for defence when software is installed outside of default locations. A little tip for offence when software is installed outside of default locations.
This is a useful tip for IT/Infosec concerned about application security in their infrastructure, not to be confused with ‘appsec’ web apps/API’s I mean installing programs internally, on Windows, and it’s also useful if you’re on the offensive side and you aint got much to work with.
The Skinny
When a program is installed and that program requires admin rights it tends to traditionally be installed in Program Files, or Program Files x86 and when the program is finalising it’s installation it applies access controls via inheritance from those traditional locations, basically it’s inheriting ACL’s that allow only admin and elevated accounts can write and delete in these places, all can read and copy but no write, no delete.
The problem is, this inheritance is issued from a relative address (parent) not an absolute C:\Program Files\, what that means is the installer assumes the folder above the program is Program Files, or Program Files x86 etc … but doesn’t factor in during the installation process it affords the person installing the opportunity to change the installation site, let’s say for example you had storage concerns on C:\ so you decided to stick it in D:\ the permissions will be completely useless opening up attack surface to overwrite, patch or position binaries within those folders for other bugs developers haven’t cleaned up or defended against.
Remediation:
The best I have means that the alternative install location has to be NTFS formatted filesystem
Get-Acl -Path C:\Program Files\ | Set-Acl -Path D:\coolprogram\
Proof of Concept
If we take the Global Protect Installer as an example, and it really could be any other software, as it's more a 'Installer' software issue than the actual software it's installing, I mean, software providers should all inherit some concern and have a conversation about this if they can, but what I'm saying is, I'm not picking on Palo Alto, they're just what I had in my Download folder.
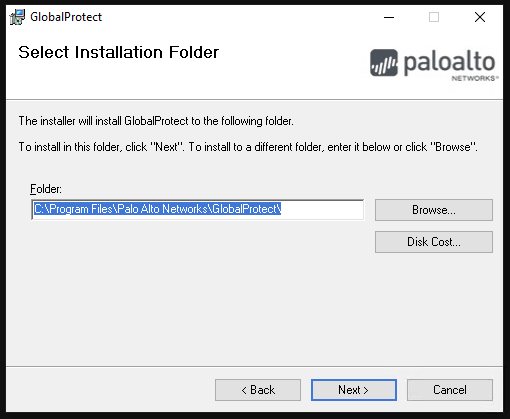
As the option is presented most of us will never change this, ever. the only thing to do here is hit Next >
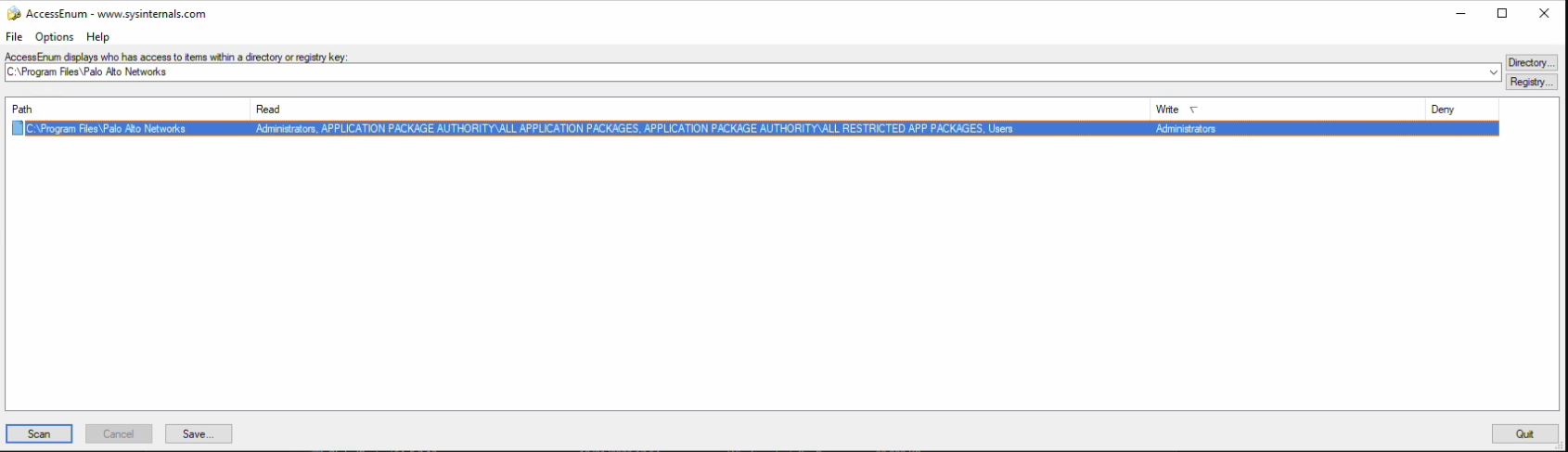
| Path | Read | Write |
|---|---|---|
| C:\Program Files\Palo Alto Networks | Administrators, APPLICATION PACKAGE AUTHORITY\ALL APPLIATION PACKAGES,APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APP PACKAGES, Users | Administrators |
As you see above only Administrators can write to the installed folder, as it should be, as it is, as you would expect, but below the permissions arent adjusted to the new location, nor is the user made aware of such a change in security direction. this has more to do with the installer software than anything else
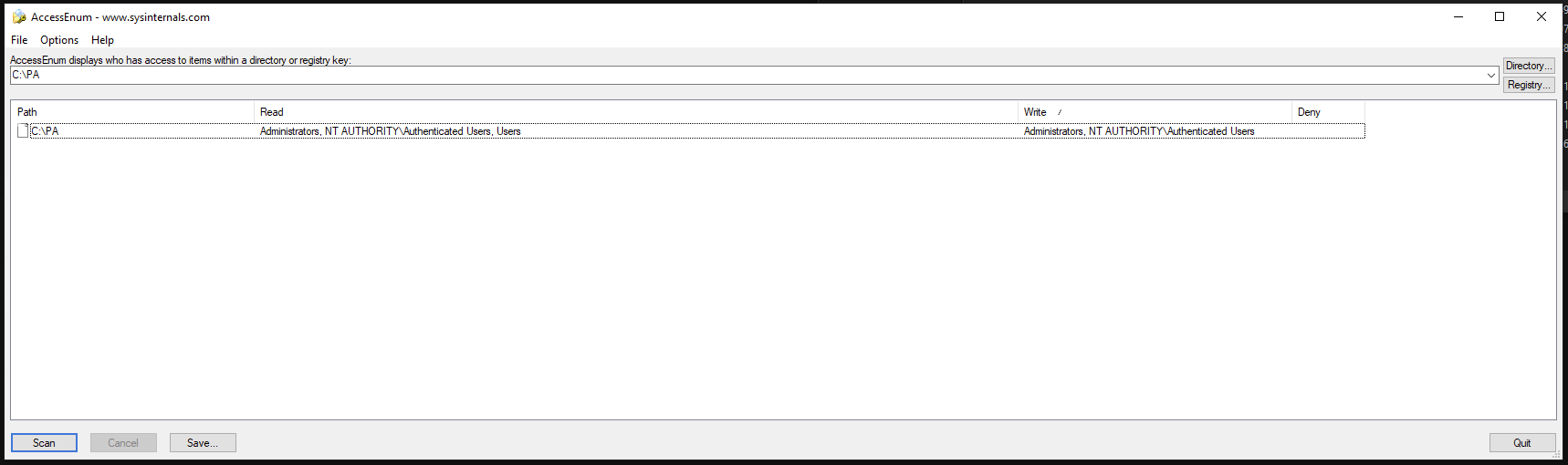
| Path | Read | Write |
|---|---|---|
| C:\PA\ | Administrators, NT AUTHORITY\Authenticated Users, Users | Administrators, NT AUTHORITY\Authenticated Users |
If you want something more interactive than screenshots you can hear me screencast an 8 minute video here: https://www.youtube.com/watch?v=r5zKinHB2RI